Join us in Atlanta on April 10th and explore the landscape of security workforce. We will explore the vision, benefits, and use cases of AI for security teams. Request an invite here. The open-source Ray framework is ubiquitous — thousands of organizations use it to run complex, intensive workloads. GPT-3 was trained on it, and […]
Read MoreTag: Cloud and Data Storage Security
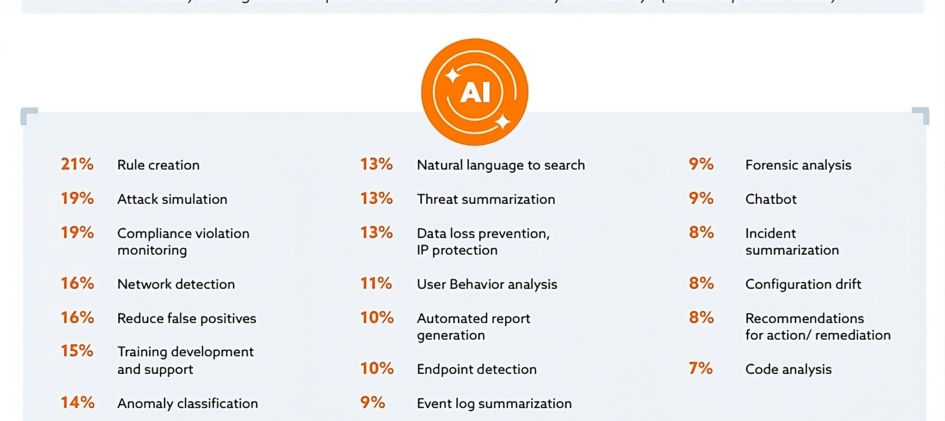
Google Cloud and CSA: 2024 will bring significant generative AI adoption in cybersecurity, driven by C-suite
Join us in Atlanta on April 10th and explore the landscape of security workforce. We will explore the vision, benefits, and use cases of AI for security teams. Request an invite here. The “department of no” stereotype in cybersecurity would have security teams and CISOs locking the door against generative AI tools in their workflows. […]
Read More
Can generative AI help address the cybersecurity resource gap?
Join us in Atlanta on April 10th and explore the landscape of security workforce. We will explore the vision, benefits, and use cases of AI for security teams. Request an invite here. At every cybersecurity event I attend, CISOs and other security professionals discuss the challenges of finding, hiring and maintaining a team of cybersecurity […]
Read More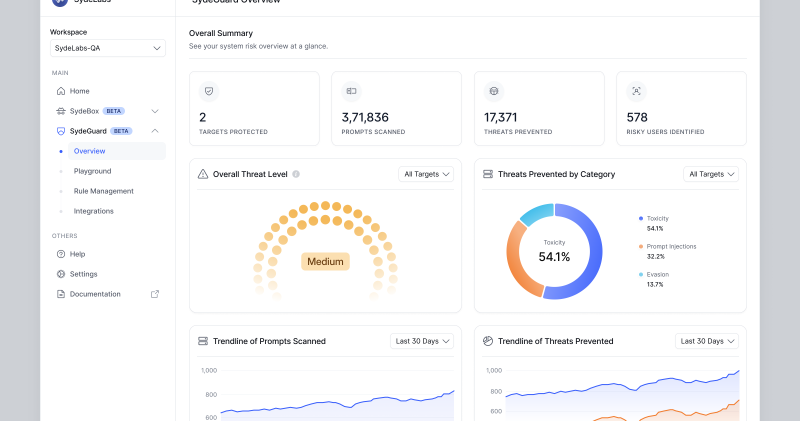
SydeLabs raises $2.5M seed to develop an intent-based firewall guard for AI
Join us in Atlanta on April 10th and explore the landscape of security workforce. We will explore the vision, benefits, and use cases of AI for security teams. Request an invite here. Generative AI is the new driving force of modern businesses, but the same technology has the potential to open the gate to entirely […]
Read More
Hacking internal AI chatbots with ASCII art is a security team’s worst nightmare
Join us in Atlanta on April 10th and explore the landscape of security workforce. We will explore the vision, benefits, and use cases of AI for security teams. Request an invite here. Insider threats are among the most devastating types of cyberattacks, targeting a company’s most strategically important systems and assets. As enterprises rush out […]
Read More